Smith Level Road is one of the primary ways into downtown Carrboro. Well known Carrboro business are located right on Smith Level Road (which changes it’s name to S Greensboro St as soon as it crosses Highway 54), including Steel String Brewery, Glass Half Full, Open Eye Cafe and the future site of a new library. However I live on the south side of highway 54, which means I have to cross highway 54, a divided highway, in order to reach downtown Carrboro. This is an easy drive, but its very dangerous to bike or walk.
Smith Level Road has loads of potential for biking and pedestrians because is underneath Highway 54! The problem is that Smith Level Road can be up to 8 lanes across!

Technically lane one (1) and lane eight (8) in the picture above are bus drop offs, but I often see cars using them to merge, and pedestrians still have to cross them just like any other lane. As stated in the picture, a Boeing 737 can literally fit between the two curbs.
This type of road is quite common in the triangle region, and its awful for pedestrians to cross, and currently has no bike lanes (not even unprotected ones). The more I bike or walk, the more I really hate turn lanes, especially right turn lanes. This particular road is even more annoying because 200 feet behind this picture, Smith Level Road has only two lanes. The road also shrinks back to two lanes right past the overpass seen in the picture. I will try to draw this out:
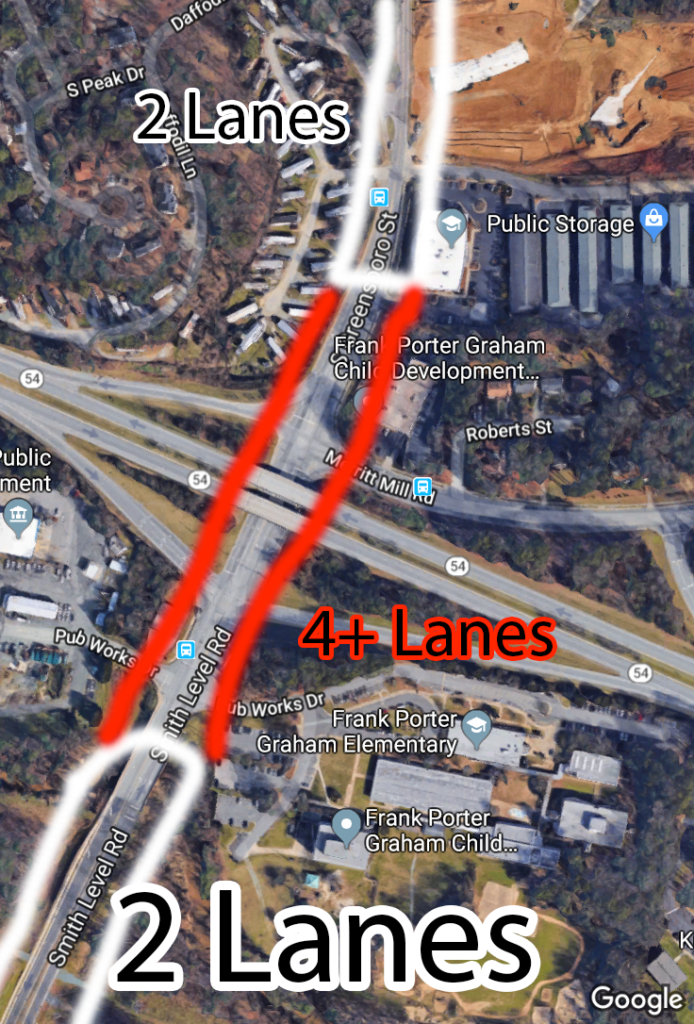
This means that the additional lanes of traffic really are not doing anything. The car throughput is exactly the same. There is also traffic circles both south and north of highway 54 meaning that it would be prohibitively expensive for Smith Level Road to ever be expanded to four lanes. Even without the traffic circles, I would wager that it will never happen because it would require demolishing many houses.
Here is another Google satellite picture of where Smith Level is seven lanes. I tried to color code each lane so it can be more easily seen:

You will also notice there is only sidewalk on one side of the road. Not pictured is the elementary school in the bottom right corner of this picture. Early in the morning you will see families try to cross this intersection to walk to school. It is insanely dangerous and I can only imagine that some of these families only have one car that is already in use by another parent, or both parents are working and kids are walking themselves to school. As a parent, I would not let my family walk to school given the current conditions of this road.
My proposal is that we perform something called a road diet. A road diet is a technique where the number of travel lanes and/or width of the road is reduced in order to achieve systemic improvements. Durham has already performed road diets on many roads, so there is a track record of success already in the triangle. You can actually see this on Durham-Chapel Hill Blvd near Foster’s Market where they reduced four lanes to two car lanes with bike lanes. I commute to Durham on this road and have noticed no additional delay at all.
I can’t imagine a better place for a road diet that Smith Level road. There is already bike lanes on the two-lane section of road south of Highway 54 connecting to the numerous neighborhoods, Culbreth Middle school and Carrboro High school. On the north side, when they complete the South Green shopping complex, there is already an existing separated bike path (named the Robertson Bike Path) that connects through neighborhoods up to Franklin Street via the Libba Cotten Bikeway. There is also an effort to complete the Morgan Creek Trail all the way to Smith Level Road. This means if we created a road-diet via my proposal, someone living in Southern Village could bike in protected bike lanes all the way to downtown Carrboro! Finally a holistic bike path from huge dense neighborhoods to downtown.
I am not a city planner, architect or civil engineer, but I pulled out Photoshop to try and envision what this could look like: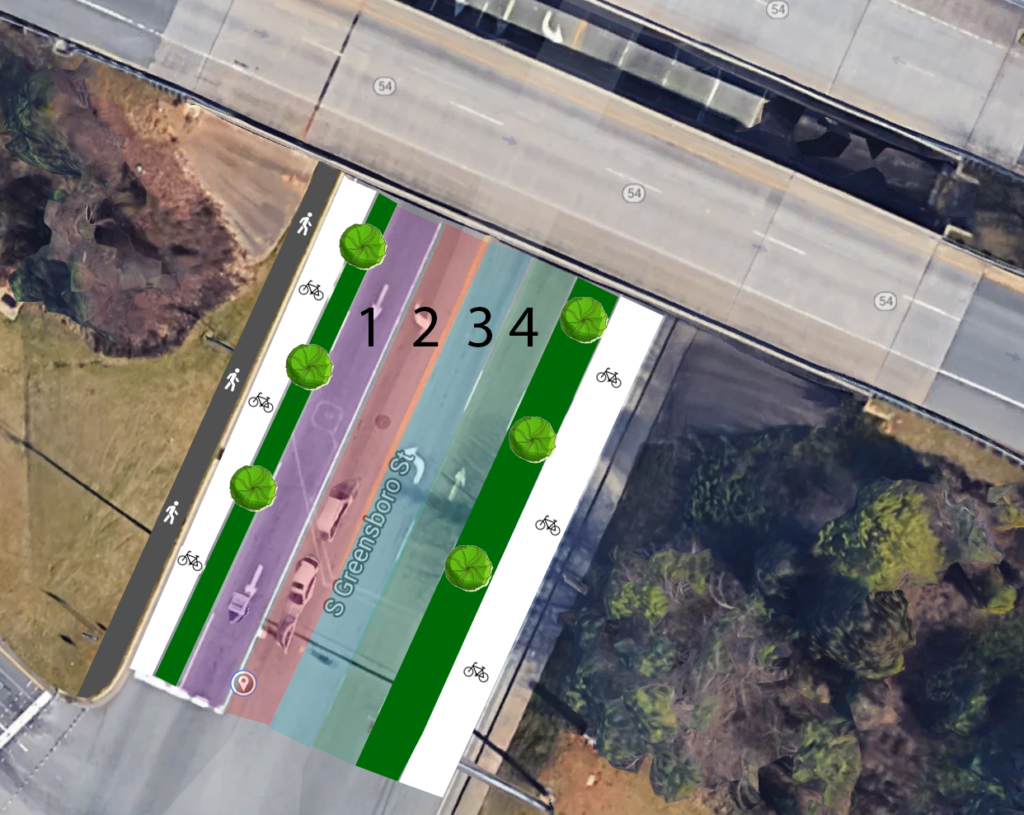
I added trees (those green circles above) as well to my protected bike planes because I think shade will encourage both bikers and pedestrians, and I recently read an article on the subject. Imagine something like this:

I am not 100% sure about how to encourage my city leaders to achieve my fantasy of a more bikeable Carrboro & Chapel Hill, but I figured I would at least write down my thoughts so others could read and comment. I hope others are as interested in this as I am. Thank you for reading.








